August 24, 2023
For years, consumers and businesses alike have been given the same cybersecurity advice: use strong passwords, back up your data on a regular basis and use multi-factor authentication where you can.
These three pillars are the foundation of what is referred to as cyber hygiene, and they help people keep their personal information secure. But now, we’re entering a new cybersecurity paradigm, one in which generative AI can be used to exploit human and technical vulnerabilities.
This raises the question: are these fundamental cyber hygiene practices enough to safeguard against new emerging AI-related cyber threats?
IEEE Senior Member Kayne McGladrey says that there are three threats commonly associated with the rise of generative AI – business email compromise, deepfakes and the generation of attack code.
“These threats are not merely theoretical, although at the moment, they are still relatively limited in their application,” McGladrey said. “It is reasonable to expect that threat actors will continue to find innovative new uses of generative AI, extending beyond business email compromise, deepfakes and the generation of attack code.”
So, let’s explore what these cyber attacks are:
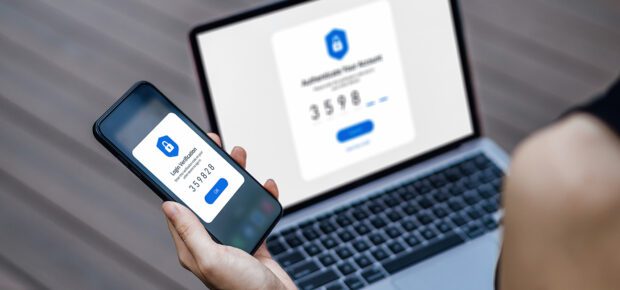
Business Email Compromise (BEC): BEC attacks involve threat actors compromising executive email accounts to manipulate individuals into performing unauthorized transactions. Traditionally, these attacks heavily relied on mimicking the writing styles of executives. However, generative AI can now emulate not just writing style, but also an executive’s writing tone, amplifying the scalability and effectiveness of BEC attacks. Multifactor authentication is seen as the best defense against email compromise.
Deepfakes: Deepfakes use AI technology to produce convincing and deceptive audio and video content. Threat actors can use deepfakes to target and impersonate individuals, potentially leading to misinformation, reputational damage and even market manipulation.
“Consumers should exercise caution and skepticism when encountering suspicious or outrageous media content. Basic cyber hygiene alone cannot adequately defend against the consumption of deepfakes,” McGladrey said.
AI-Generated Attack Code: Most malicious actors don’t have the technical skills to create new exploits or write code. Rather, they rely on previously-identified playbooks for their attacks, pulling code from the dark web. Generative AI enables threat actors to create malicious code specifically designed to exploit vulnerabilities in other systems.
Moving Beyond Basic Cyber Hygiene
Experts note that even small improvements in cyber hygiene can yield results because malicious actors tend to follow the path of least resistance.
So how can individuals and organizations supplement their basic cyber hygiene practices and enhance their security? While strong passwords, regular backups and multi-factor authentication remain essential, here are some additional recommended steps:
Use a security key: Security keys are small physical devices which usually connect to hardware via USB. They essentially act as a second form of authentication, denying access to services even when someone knows the password to an account. They cannot easily be spoofed and are not prone to phishing scams the way that other forms of multi-factor authentication are. They’re becoming increasingly common in corporate settings, and are also used by high net worth individuals and celebrities to protect access to accounts.
Regular Software Updates: Keeping operating systems and software applications up to date is crucial. This helps to patch vulnerabilities that could be exploited by malicious actors.
Benchmark Against Well-Regarded Frameworks. Organizations should follow a reputable, trustworthy source to keep updated, such as the NIST Cybersecurity Framework (CSF), or the Center for Internet Security’s Critical Security Controls (CIS-CSC), and periodically benchmark their progress against the framework.
Educating and Training: Promote cybersecurity awareness among employees, customers and individuals. This includes training on how to recognize phishing emails, the importance of not sharing passwords, and understanding the risks of public Wi-Fi.
Using a VPN: Using a Virtual Private Network (VPN) especially when connected to public Wi-Fi can help encrypt internet traffic and protect data from being intercepted.
Access Controls and Principle of Least Privilege: Organizations should limit access rights to those who need them and regularly review those rights. Implement the “principle of least privilege”, where users have the minimum levels of access to critical network operations required to perform their roles.
“In a nutshell, while the fundamentals are crucial, comprehensive cyber hygiene requires a multi-layered approach to security,” said IEEE Member Sukanya Mandal. “This involves not only technical measures but also education, policies, and practices that together build a culture of security.”
Learn more: In this issue of IEEE Privacy and Security Magazine from the IEEE Computer Society, a researcher explores the use of a generative AI tool in phishing scams, and comes to the conclusion that threat actors will use these tools for a wide range of malicious activities.




 Meaningful Momentum or Running in Place?
Meaningful Momentum or Running in Place? AI Through Our Ages
AI Through Our Ages Liquid Infrastructure: Our Planet's Most Precious Resource
Liquid Infrastructure: Our Planet's Most Precious Resource The Impact of Technology in 2025
The Impact of Technology in 2025 Quantum and AI: Safeguards or Threats to Cybersecurity?
Quantum and AI: Safeguards or Threats to Cybersecurity? Why AI Can't Live Without Us
Why AI Can't Live Without Us Bits, Bytes, Buildings and Bridges: Digital-Driven Infrastructure
Bits, Bytes, Buildings and Bridges: Digital-Driven Infrastructure Impact of Technology in 2024
Impact of Technology in 2024 Emerging AI Cybersecurity Challenges and Solutions
Emerging AI Cybersecurity Challenges and Solutions The Skies are Unlimited
The Skies are Unlimited Smart Cities 2030: How Tech is Reshaping Urbanscapes
Smart Cities 2030: How Tech is Reshaping Urbanscapes Impact of Technology 2023
Impact of Technology 2023 Cybersecurity for Life-Changing Innovations
Cybersecurity for Life-Changing Innovations Smarter Wearables Healthier Life
Smarter Wearables Healthier Life Infrastructure In Motion
Infrastructure In Motion The Impact of Tech in 2022 and Beyond
The Impact of Tech in 2022 and Beyond Cybersecurity, Technology and Protecting Our World
Cybersecurity, Technology and Protecting Our World How Technology Helps us Understand Our Health and Wellness
How Technology Helps us Understand Our Health and Wellness The Resilience of Humanity
The Resilience of Humanity Harnessing and Sustaining our Natural Resources
Harnessing and Sustaining our Natural Resources Creating Healthy Spaces Through Technology
Creating Healthy Spaces Through Technology Exceptional Infrastructure Challenges, Technology and Humanity
Exceptional Infrastructure Challenges, Technology and Humanity The Global Impact of IEEE's 802 Standards
The Global Impact of IEEE's 802 Standards Scenes of our Cyber Lives: The Security Threats and Technology Solutions Protecting Us
Scenes of our Cyber Lives: The Security Threats and Technology Solutions Protecting Us How Millennial Parents are Embracing Health and Wellness Technologies for Their Generation Alpha Kids
How Millennial Parents are Embracing Health and Wellness Technologies for Their Generation Alpha Kids Space Exploration, Technology and Our Lives
Space Exploration, Technology and Our Lives Global Innovation and the Environment
Global Innovation and the Environment How Technology, Privacy and Security are Changing Each Other (And Us)
How Technology, Privacy and Security are Changing Each Other (And Us) Find us in booth 31506, LVCC South Hall 3 and experience the Technology Moon Walk
Find us in booth 31506, LVCC South Hall 3 and experience the Technology Moon Walk Virtual and Mixed Reality
Virtual and Mixed Reality How Robots are Improving our Health
How Robots are Improving our Health IEEE Experts and the Robots They are Teaching
IEEE Experts and the Robots They are Teaching See how millennial parents around the world see AI impacting the lives of their tech-infused offspring
See how millennial parents around the world see AI impacting the lives of their tech-infused offspring Take the journey from farm to table and learn how IoT will help us reach the rising demand for food production
Take the journey from farm to table and learn how IoT will help us reach the rising demand for food production Watch technical experts discuss the latest cyber threats
Watch technical experts discuss the latest cyber threats Explore how researchers, teachers, explorers, healthcare and medical professionals use immersive technologies
Explore how researchers, teachers, explorers, healthcare and medical professionals use immersive technologies Follow the timeline to see how Generation AI will be impacted by technology
Follow the timeline to see how Generation AI will be impacted by technology Learn how your IoT data can be used by experiencing a day in a connected life
Learn how your IoT data can be used by experiencing a day in a connected life Listen to technical experts discuss the biggest security threats today
Listen to technical experts discuss the biggest security threats today See how tech has influenced and evolved with the Games
See how tech has influenced and evolved with the Games Enter our virtual home to explore the IoT (Internet of Things) technologies
Enter our virtual home to explore the IoT (Internet of Things) technologies Explore an interactive map showcasing exciting innovations in robotics
Explore an interactive map showcasing exciting innovations in robotics Interactively explore A.I. in recent Hollywood movies
Interactively explore A.I. in recent Hollywood movies Get immersed in technologies that will improve patients' lives
Get immersed in technologies that will improve patients' lives